Biometric Security Measures Include Which of the Following
Biometric systems first require a person to establish his or her identity in the system. Up to 20 cash back Some security systems also include additional features such as age gender and height in biometric data to thwart hackers.

Security Measures To Be Taken While Developing A Mobile Application Mobileapps Mobile Application Mobile App Development Companies Mobile App Development
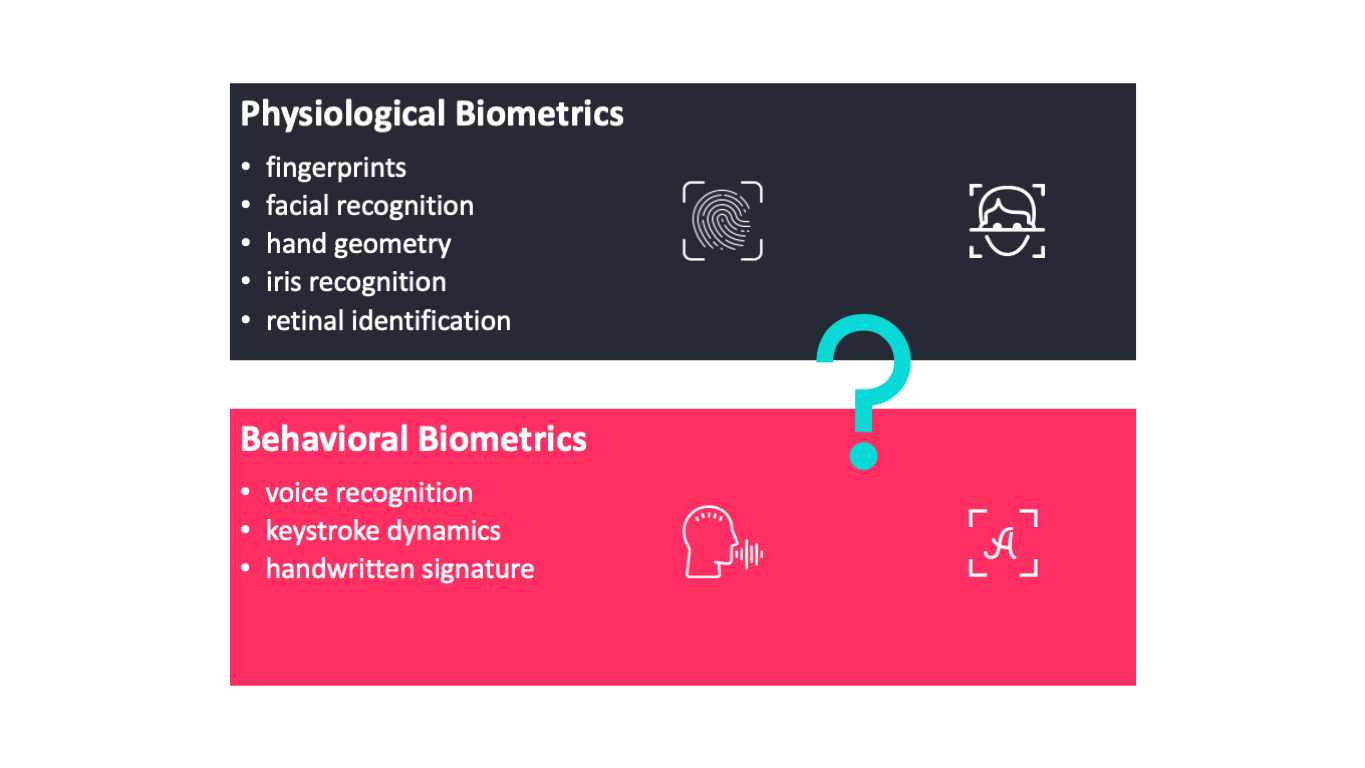
The two main types of biometric identifiers are either physiological characteristics or behavioral characteristics.

. This biometrics type includes but is not limited to the following. Physiological biometrics include mark all that apply. 5 Biometric Security Measures to Keep You Safer in 2019.
Hand geometry biometric systems incorporate the salient features of finger geometry but also include the surfaces of the hand itself and its side profile. Different Types of Physiological Biometrics. However the known types of biometrics are following.
Static methods are based on the physiological characteristics of a person present throughout their life. Biometric identification methods include the following. Physiological biometrics refers to the physiological features of a person by which he or she is recognized.
These features include facial features fingerprints iris and retina patterns. Biometrics are physical security mechanisms which deny any unauthorised access via authentication. Biometrics is a branch of information technology that aims towards establishing ones identity based on personal traits.
With behavioral biometrics on the other hand the system analyzes any pattern of behavior that is. Behavioral biometrics are including signature and voice recognition. Physical biometrics analyze facial features eye structure hand shape and other things involving your bodys physical form.
Physiological identifiers relate to the composition of the user being authenticated and include the following. There are two main types of biometrics used for securityphysical and behavioral. Individuals produce a distinctive heartbeat regardless of their heart rate and level of exertion that is determined by a number of factors.
These can include physiological traits such as fingerprints and eyes or behavioral characteristics such as the unique way youd complete a security-authentication puzzle. This security process is referred to as biometric authentication and is reliant on individuals unique biological characteristics to identify the individual correctly. The identification of the individual becomes.
Facial recognition gait analysis and behavioral palm and voice biometrics are some of todays cutting-edge biometric technologies that. There are two types of biometrics. To be useful biometric data must be unique permanent and collectible.
Traditional security and biometric security. Biometric security is the use of technological devices for identity verification through physical or behavioral characteristics. Biometrics is presently a buzzword in the domain of information security as it provides high degree.
Which of the following security measures is a form of Biometrics. Indias Unique ID Authority of India Aadhaar program is a good example. These traits can be used instead of passwords to verify and identify individuals as they are bound to the individual.
Enrollment and verification in a typical biometric system. I width of the finger at various places ii length of each of the fingers iii palm area thickness. Which of the following biometric security measures compares the length of each finger the translucence of fingertips and the webbing between fingers against stored data to verify users identities.
These features include face and hand geometry iris vein patterns and other features. The most common performance metrics are the FAR false acceptance rate and the FRR false rejection rate. Physiological biometrics are including fingerprint iris face palm vein recognition.
Finger geometry the size and position of fingers iris recognition. The security measures we take can be largely divided into two major categories. Fingerprint recognition which measures a fingers unique ridges is one of the oldest forms of biometric identification.
The security of the biometric authentication data is vitally important even more than the security of passwords since passwords can. All biometric modalities are basically two types. Different metrics can be used for the purpose.
This article takes a comparative approach to discuss traditional and biometric approaches of security and tries to draw a. Iv translucence of the fingertips. _____ security measures primarily control access to computers and networks and they include devices for securing computers and peripherals from theft.
Initiated in 2009 the multi-step authentication program incorporates iris scans fingerprints from all 10 fingers and facial recognition. Know the definition of biometric security and explore recognition. Fingerprint recognition - This relies on matching the unique print patterns found on one or more fingers.
The hand geometry recognition is one of the biometric security meaures and it takes advantage of the structure of the palm and fingers by measuring certain features of the hand such as. Morphological identifiers mainly consist of fingerprints the hands shape the finger vein. They can be either morphological or biological.
A corporate office recently had a security audit and the IT manager has decided to implement very strict security standards. In the world market for biometric security static methods are mainly represented. Physiological biometrics are those that rely on ones physical characteristics to determine identity.
The term Biometrics is composed of two words Bio Greek word for Life and Metrics Measurements. Once measured the information is compared and matched in a database.

San Diego Biometric Digital Security It Services Computer Security San Diego Biometrics Biometric Security Computer Security

Measuring Your Biometrics 18 X 24 Poster Health Poster Biometrics Health Screening Health

Biometric Mastercard With Fingerprintreader For More Security Measures Https Www Tigmoo Com Blog Biometric Card W Biometrics Fingerprint Reader Mastercard
Biometric Authentication Methods Fingerprints Facial Recognition Hand By Anh T Dang Towards Data Science

Training Oak Tree Business Credit Union Marketing Career Growth Financial Institutions

What Is Biometric Payment And How Does It Work

Advanced Biometric Technology To Be Deployed Globally Ihls Biometrics Biometric Authentication Learning Technology

Biometric Security Biometric Security Biometrics Technology

Biometric Access Control Systems Security Measures And Principles
Comments
Post a Comment